Bind vs. Reverse Shells
In ethical hacking, bind shells and reverse shells are two different methods of establishing a remote connection between an attacker and a target machine.
Bind Shell
The target machine opens a network port and listens for incoming connections. The attacker then connects to this open port from their machine. The target machine initiates the bind shell by opening a port and waiting for a connection. The attacker needs direct access to the target machine’s network, which means the target machine must have an open port that is accessible (e.g., no firewalls blocking incoming connections). Since the target machine is waiting for a connection, this approach may be more detectable, and firewalls or network security tools may block the open port.
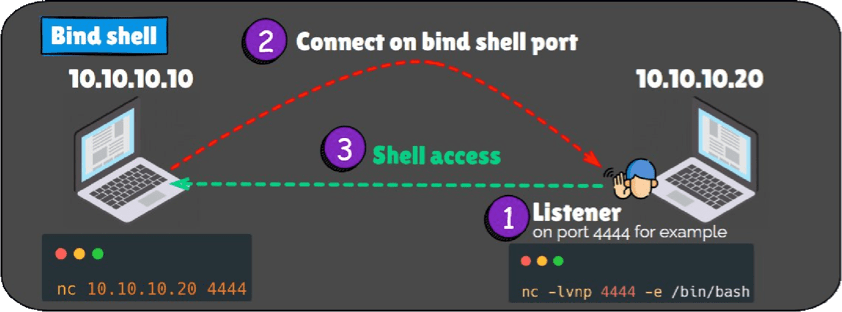
Example: The target machine runs a command to listen on port 4444, and the attacker connects to this port to gain access.
Reverse Shell
The target machine connects back to the attacker’s machine, allowing the attacker to control the target machine through the connection. The attacker sets up a listener on their machine and waits for the target machine to connect back. This is often more effective in environments where outbound connections (from the victim machine to the attacker) are allowed through firewalls, but inbound connections (to the victim) are blocked. A reverse shell is often stealthier because firewalls typically allow outgoing connections from internal machines, making it harder to detect.

Example: The attacker waits for a connection on their machine (e.g., listening on port 4444), and the target machine initiates a connection to the attacker, giving them control.
Key Differences
| Aspect | Bind Shell | Reverse Shell |
| Connection Initiation | Target (victim) opens a port and waits for the attacker to connect. | Attacker sets up a listener, and the target (victim) connects back to the attacker. |
| Network Accessibility | Attacker needs direct access to the victim’s network (open port). | Works even if the victim is behind a firewall, as long as outbound connections are allowed. |
| Direction of Connection | Attacker connects to the target. | Target connects to the attacker. |
| Firewall Bypass | Harder to bypass firewalls since inbound connections are often blocked. | Easier to bypass firewalls because outbound connections are usually allowed. |
| Stealth | Less stealthy; the victim listens for connections, making it easier to detect. | More stealthy; the victim connects back, exploiting permitted outbound connections. |
| Usage | Less common in modern ethical hacking due to network restrictions. | More commonly used due to its ability to bypass firewalls and outbound connection permissions. |

Leave a comment